How to enable full GitHub clone with AWS CodePipeline?

Introduction
AWS CodePipeline is a managed service from Amazon Web Services (AWS) that allows developers to build, test and deploy their applications. It is a continuous delivery service that helps you automate your release pipelines for fast and reliable application and infrastructure updates. CodePipeline automates the build, test, and deploy phases of your release process every time there is a code change, based on the release model you define.
In this tutorial, we will look into how you can enable entire Git clone with AWS CodePipeline.
Pre-requisites
Before we start, make sure you have the following:
- A GitHub account
- A GitHub repository
How to integrate GitHub with AWS CodePipeline?
AWS CodePipeline can be integrated with multiple source actions providers like ECR, S3, GitHub and CodeCommit. In this tutorial, we will create a new CodePipeline project that uses GitHub as the source action provider.
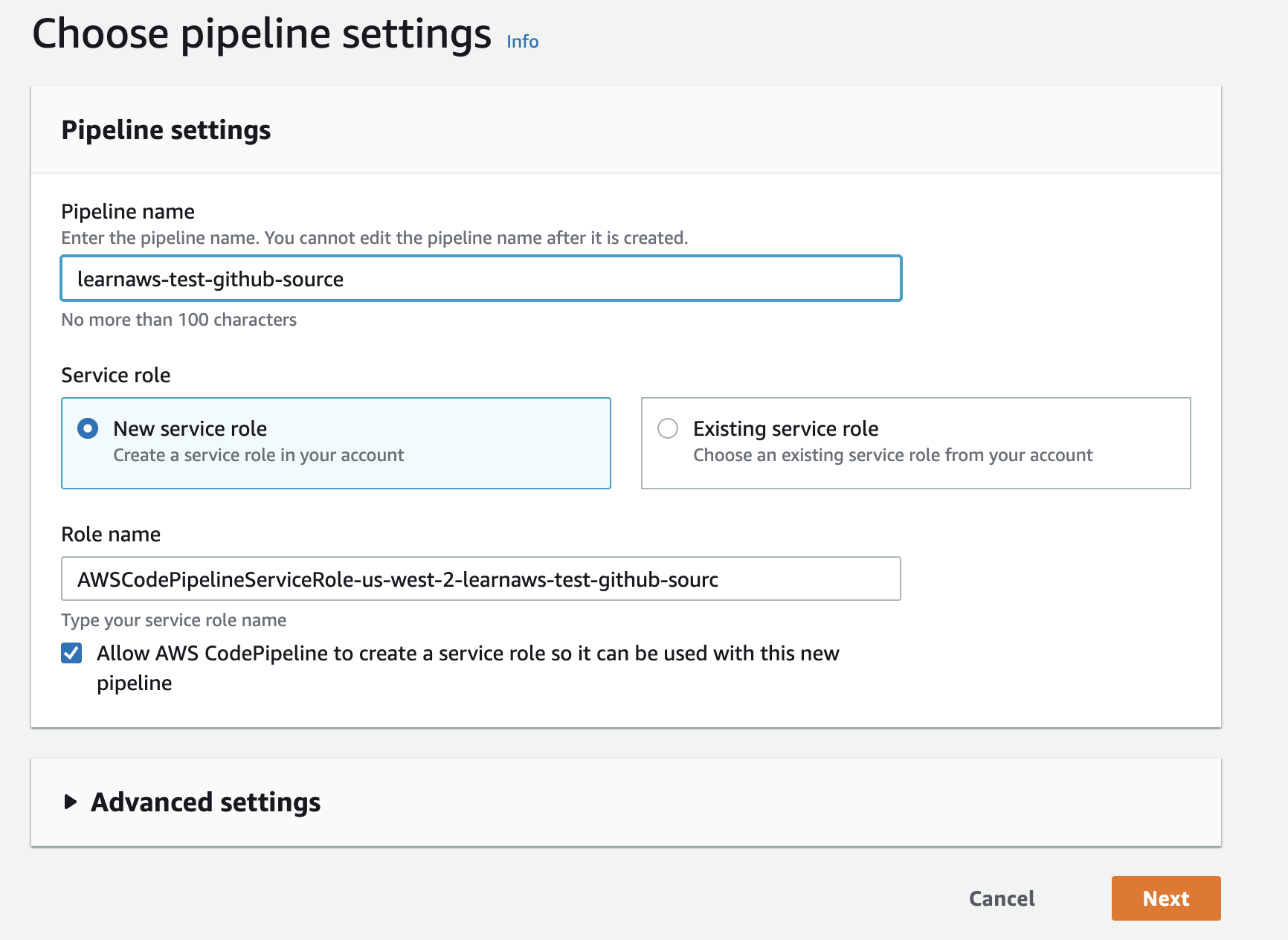
Step 1: Create a new CodePipeline project
To create a new CodePipeline project, go to the AWS CodePipeline console and click on the Create pipeline button.
Step 2: Configure the source action
Choose GitHub as the source provider:
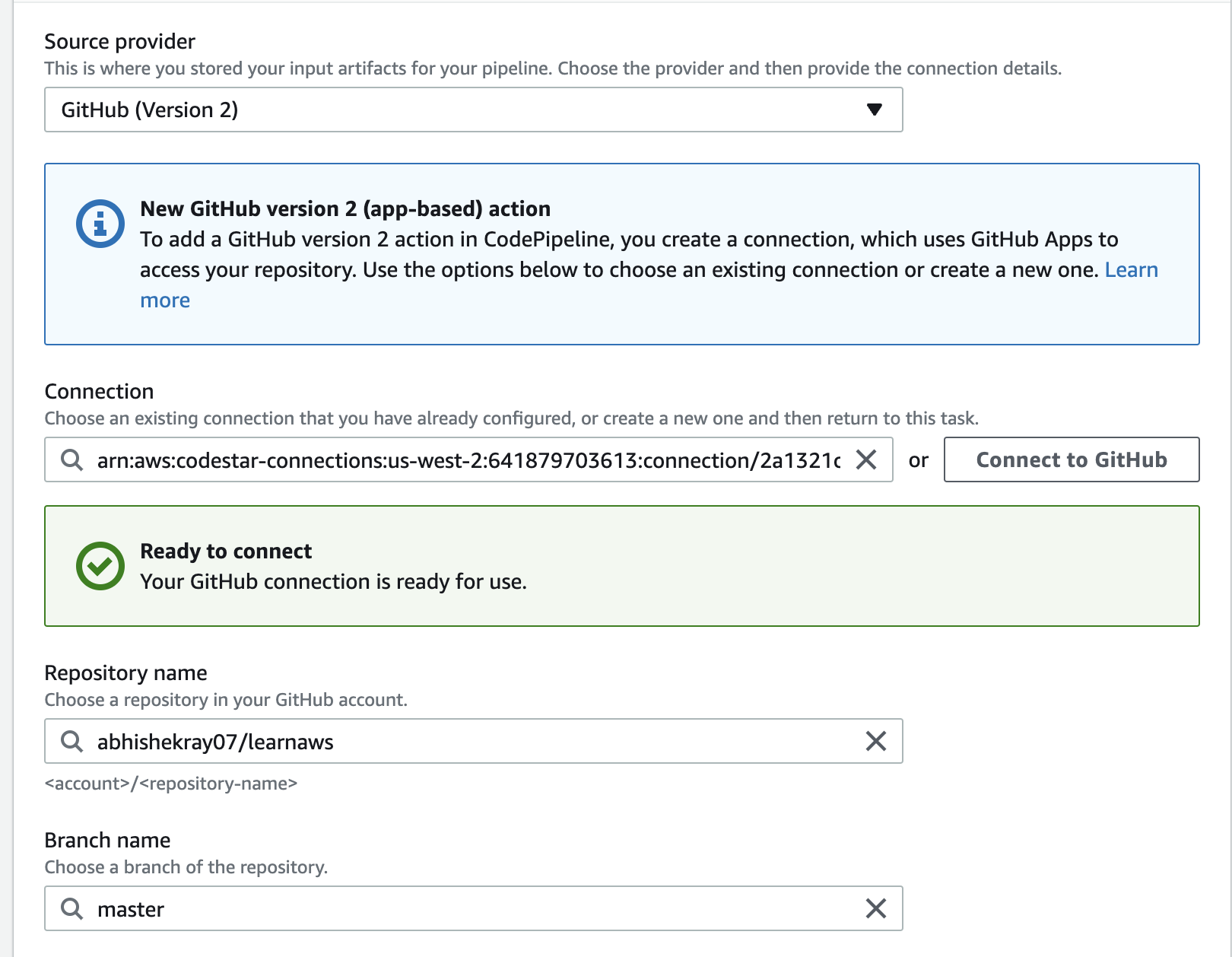
If you haven’t set up a GitHub connection before, you will be asked to connect your GitHub account to AWS CodePipeline. Click on the Connect to GitHub button and follow the instructions to connect your GitHub account. Once you have connected your GitHub account, you will be able to select your GitHub repository from the list of repositories.
![AWS CodePipeline GitHub Connection][aws-codepipeline-github-connection]
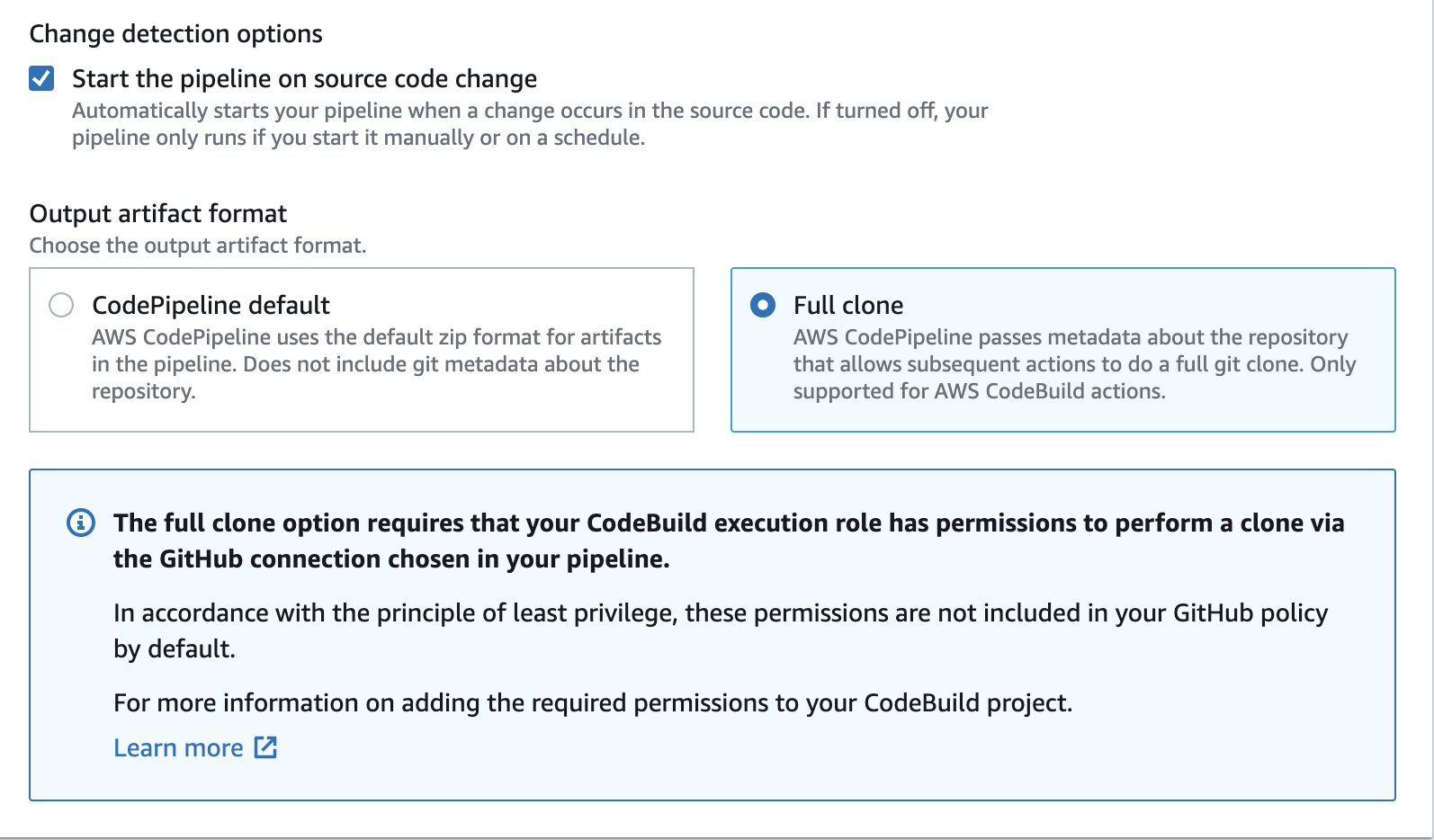
Step 3: Choose full clone
Choose the option for Full clone to enable full Git clone of the repository:
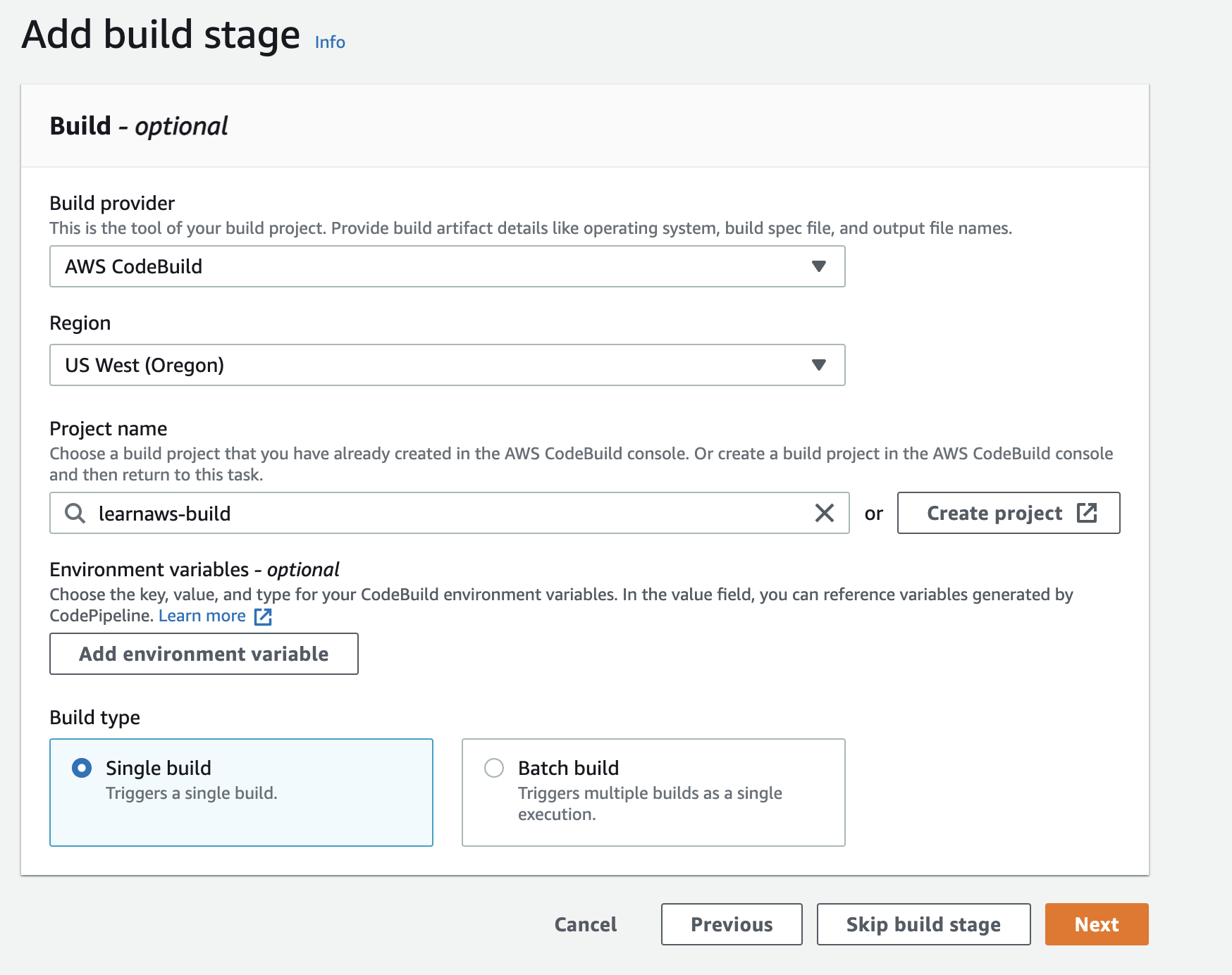
Step 4: Configure the build action
Choose the build provider as AWS CodeBuild and create a new build project. You can also choose an existing build project if you have already created one. For this tutorial, we will create a new build project. Click on the Create project button to create a new build project.
We will use the following buildspec.yaml file for this tutorial:
version: 0.2
env:
git-credential-helper: yes
phases:
pre_build:
commands:
- ls -lt
build:
commands:
- git log | head -100
- git status
post_build:
commands:
- echo "Success"
Step 5: Configure CodeBuild service IAM Role
The initial pipeline run will fail with the following error:
[Container] 2022/11/24 15:49:46 going inside waitForAgent
[Container] 2022/11/24 15:49:46 Waiting for agent ping
[Container] 2022/11/24 15:49:47 Waiting for DOWNLOAD_SOURCE
authorization failed for primary source and source version cc6abb8e2bc14f98a99e4f83cb9a8f88e839ed66
This is because the CodeBuild service role does not have the required permissions to access the GitHub repository. To fix this, we need to add the following policy to the CodeBuild service role:
{
"Version": "2012-10-17",
"Statement": [{
"Effect": "Allow",
"Action": [
"codestar-connections:UseConnection"
],
"Resource": [
"*"
]
}]
}
Step 6: Run the pipeline
Once you have added the policy to the CodeBuild service role, you can run the pipeline again. The pipeline should run successfully and you should be able to see the following output:
[Container] 2022/11/25 16:40:25 Phase complete: PRE_BUILD State: SUCCEEDED
[Container] 2022/11/25 16:40:25 Phase context status code: Message:
[Container] 2022/11/25 16:40:25 Entering phase BUILD
[Container] 2022/11/25 16:40:25 Running command git log | head -100
commit cc6abb8e2bc14f98a99e4f83cb9a8f88e839ed66
Author: Abhishek Ray <[email protected]>
Date: Tue Nov 22 08:44:45 2022 -0800
New blog post: codebuild build failure
...
[Container] 2022/11/25 16:40:25 Running command git status
Not currently on any branch.
nothing to commit, working tree clean
Conclusion
In this tutorial, we looked into how you can enable full Git clone with AWS CodePipeline. We also looked into how you can fix the build failure that occurs when you try to run the pipeline for the first time.