How to integrate AWS CodeBuild and AWS Secrets Manager?

Introduction
AWS CodeBuild is a managed service from Amazon Web Services (AWS) that allows developers to build applications without having to manage servers. This makes it easier for them to build, test and deploy their services.
AWS CodeBuild has become very popular because it helps developers create and run builds faster, cheaper, and with less effort. The service provides a graphical interface where they can choose from over 200 prebuilt templates that contain code snippets and other resources needed to complete tasks.
CodeBuild is a cloud-based service that automates the entire deployment process. It enables developers to upload source files, configure environments, and then execute commands to build and test projects. Once built, the resulting artifacts are stored in S3 buckets and can be accessed through APIs.
How to access secrets in AWS CodeBuild?
You should never hardcode your secrets in your code. Instead, you should use a secrets manager to store your secrets and then access them in your build using environment variables. There are a couple of benefits of doing this:
- Your secrets won’t get leaked even if your source code is public.
- You can easily change your secrets without having to change your code.
How to use AWS Secrets Manager in AWS CodeBuild?
AWS Secrets Manager is a service that helps you store, manage, and retrieve secrets. It is a fully managed service that makes it easy for you to rotate, manage, and retrieve secrets throughout their lifecycle.
AWS CodeBuild integrates natively with AWS Secrets Manager. This means that you can easily access your secrets in your build using environment variables.
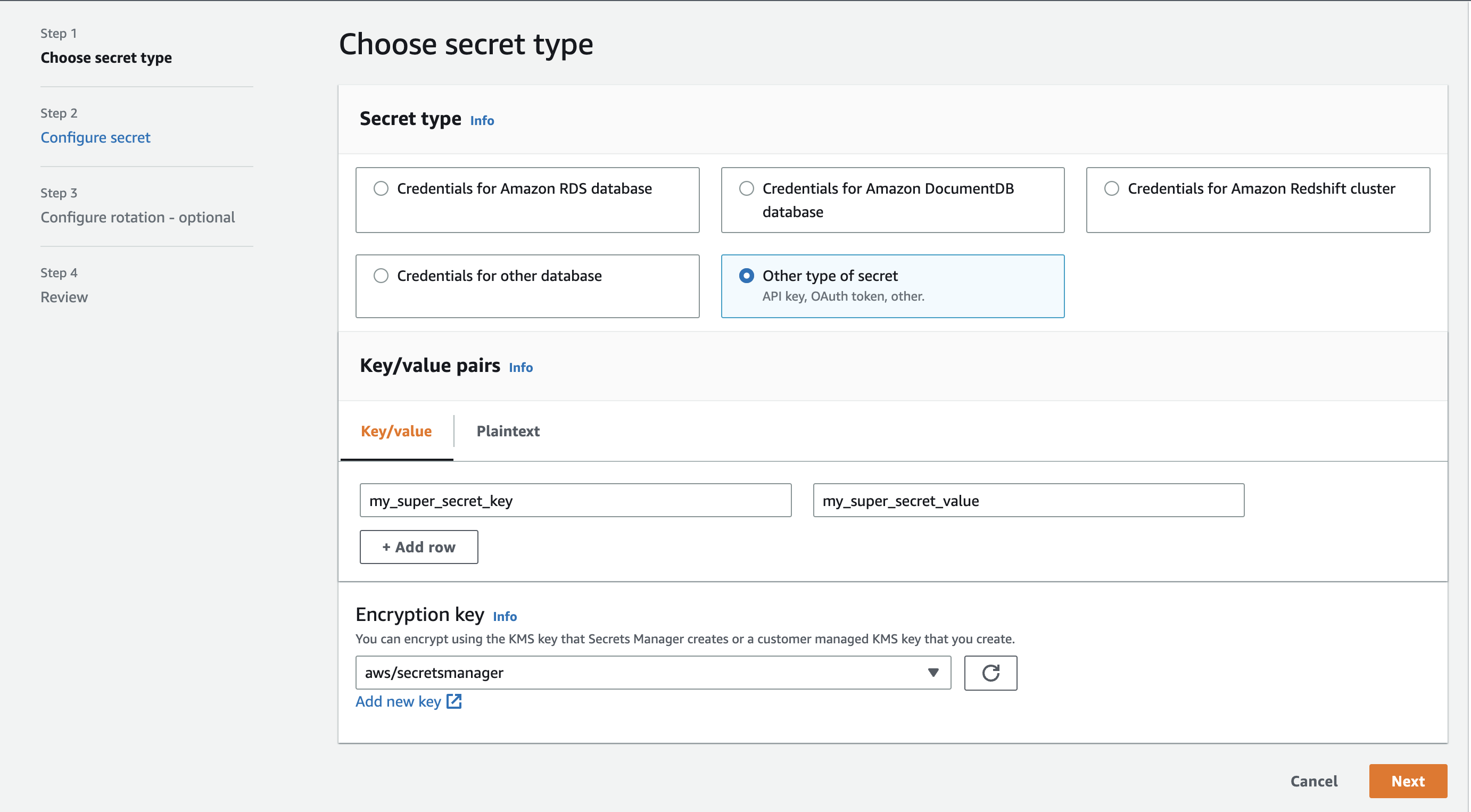
Step 1: Create a secret in AWS Secrets Manager
First, let’s create a new secret in AWS Secrets Manager that will be used in our build. Note down the ARN of the secret as we will need it later.
Step 2: Create a build project in AWS CodeBuild
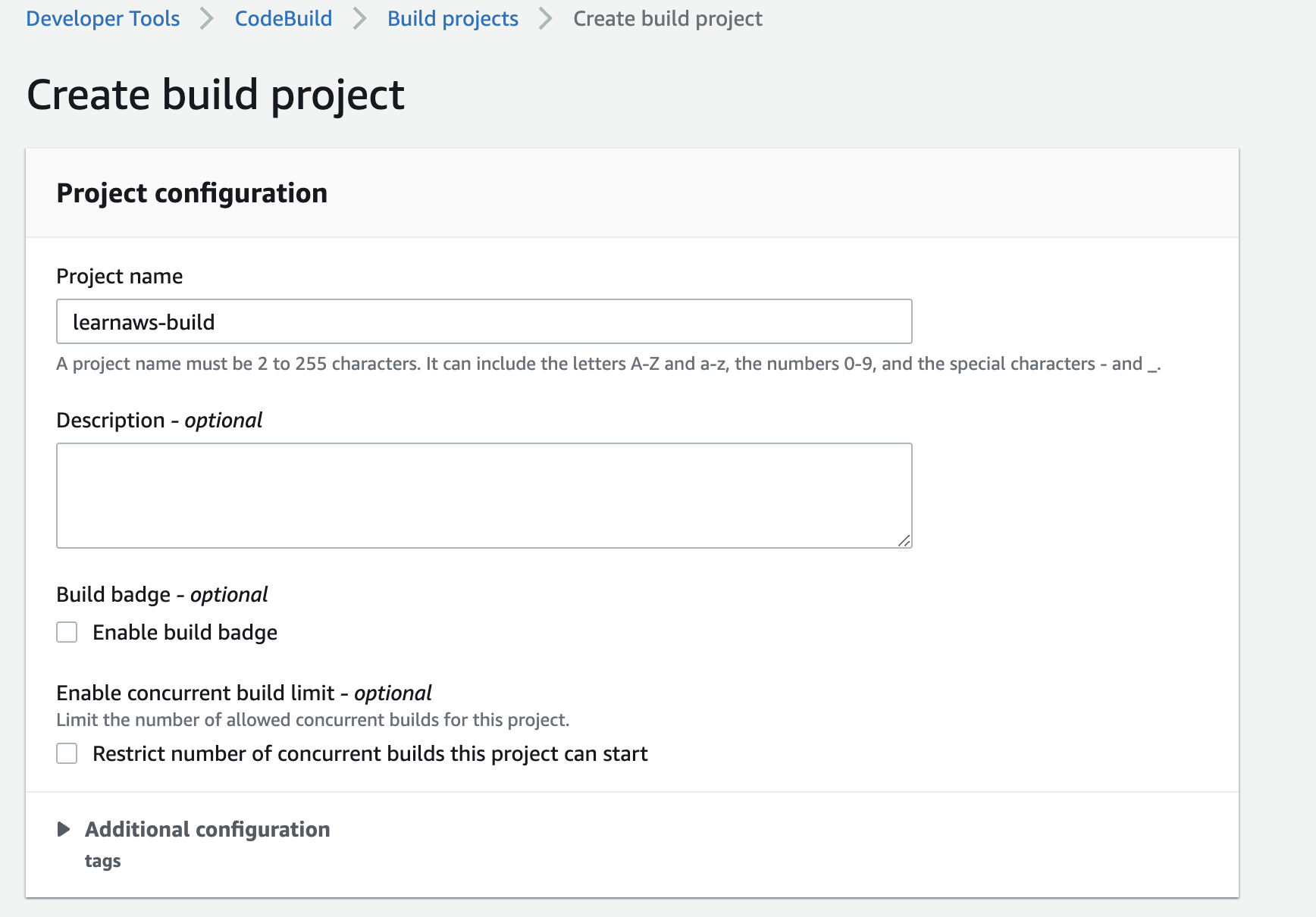
Next, let’s create a new build project in AWS CodeBuild. For simplicity, we will use the AWS Console to create a new project. You can also use the AWS CLI or the AWS SDKs to create a new project.
For ths tutorial, we will use the following settings:
- No source provider.
- Managed Ubuntu image with linux environment
Step 3: Add environment variables to your build
Now, let’s add environment variables to our build. We will use the ARN of the secret that we created in the previous step. The format of the ARN is defined by AWS and it looks like this:
<secret-id>:<json-key>:<version-stage>|<version-id>
secret-id refers to the name or ARN of the secret and is required.
The json-key is optional and it is used to retrieve a specific key from the secret. If you don’t specify a json-key, then the entire secret will be returned.
This is what the buildspec.yml file will look like:
version: 0.2
env:
secrets-manager:
SECRET_VALUE: "arn:aws:secretsmanager:us-west-2:xxxx:secret:learnaws/test/secret-l3IJg9:my_super_secret_key"
phases:
build:
commands:
- echo $SECRET_VALUE
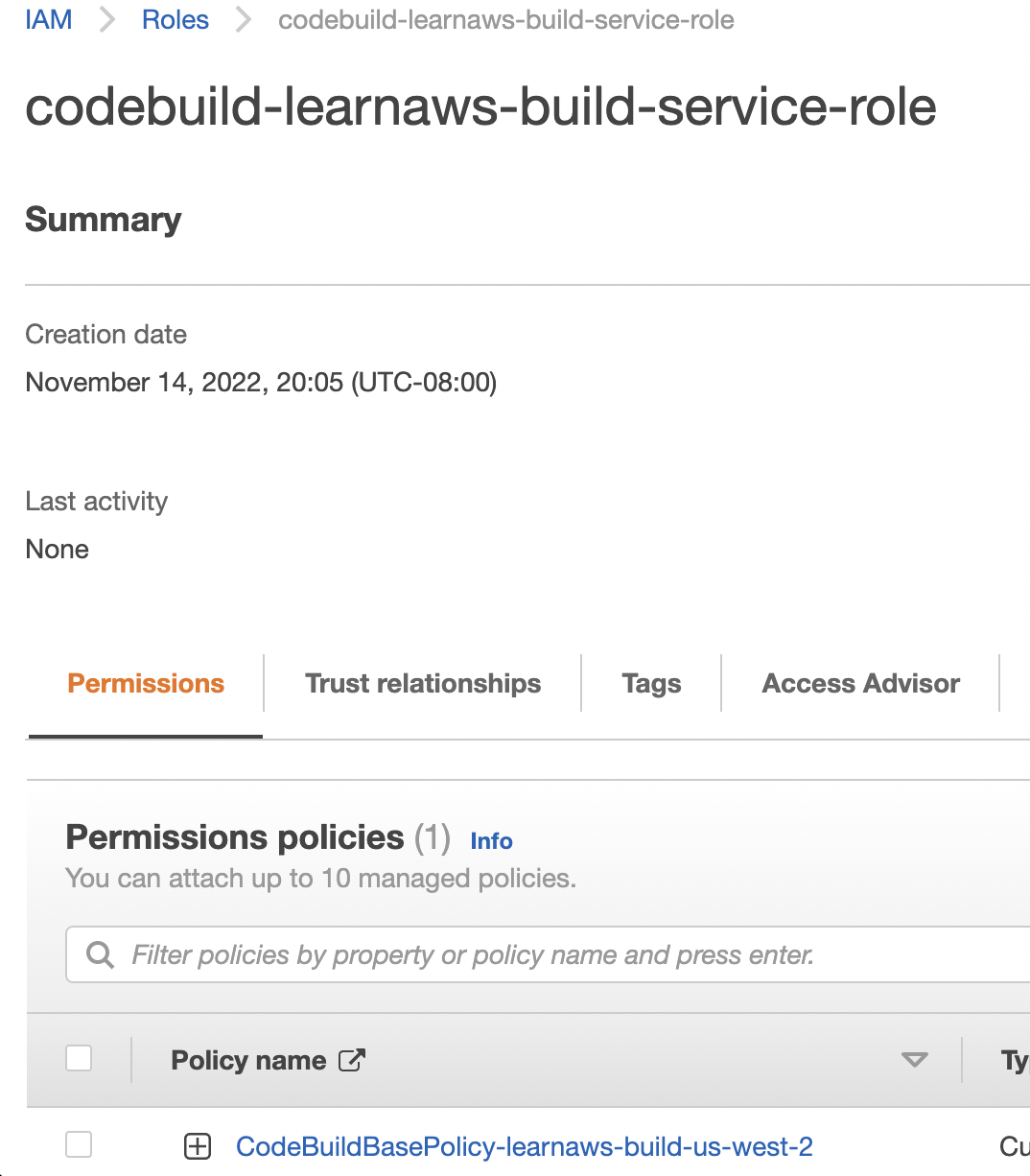
Step 4: Add IAM permissions to your codebuild service role
Now, let’s add IAM permissions to our codebuild service role. We will use the AWS Console to add the permissions. You can also use the AWS CLI or the AWS SDKs to add the permissions.
You need to add permissions to the IAM role that was created by CodeBuild for your build project. You can find the role in the IAM console. We will create a new IAM policy that has the permission to access the secret that we created in the previous step.
The IAM policy will look this:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": "secretsmanager:GetSecretValue",
"Resource": "arn:aws:secretsmanager:us-west-2:xxxx:secret:learnaws/test/secret-l3IJg9"
}
]
}
Next, attach this IAM policy to the IAM role belonging to your CodeBuild project.
Step 5: Run the build
Now, let’s run the build. You can do this by clicking on the “Start build” button in the AWS Console.
If everything is configured correctly, you should see the secret value in the build logs. This is what the build logs will look like:
[Container] 2022/11/15 04:21:23 Running command echo $SECRET_VALUE
***
Conclusion
In this article, we learned how to integrate AWS CodeBuild and AWS Secrets Manager. We also learned how to access secrets in AWS CodeBuild using environment variables.