What are the differences between AWS Public and Private Subnets?

Introduction
Networking in AWS is complicated. Understanding AWS networking concepts and how they work together is essential to ensure that your services are secure and have internet connectivity.
Before looking at the differences between Public & Private subnets, let’s go through AWS networking fundamentals.
Table of contents
AWS Virtual Private Cloud (VPC)
A VPC is your private network within AWS. A VPC isolates your resources from everyone else’s.
Each AWS account comes with a default VPC that is pre-configured for you to start using immediately. A VPC can span multiple availability zones in a region.
A VPC only exists in one AWS region.
CIDR Blocks
When creating a VPC, you must specify a range of IPv4 addresses for the VPC in the form of a Classless Inter-Domain Routing (CIDR) block. E.g., 172.31.0.0/16 is the primary CIDR block for your VPC. It defines 65536 IPv4 addresses in your VPC.
Internet Gateway (Igw)
An Internet Gateway is a VPC component that allows communication between the VPC and the Internet.
Subnets
A subnet is a range of IP addresses in your VPC. The subnet must use a CIDR block that falls within the assigned VPC.
You can create multiple subnets within a VPC. A subnet can logically group resources based on your requirements.
Examples of when you would create different subnets:
Deploying to multiple Availability Zones (AZs)
A subnet can only span one AZ. A subnet can only span one AZ. You need multiple subnets if you want to deploy your services to multiple availability zones.
Securing your resources inside a private subnet
A private subnet doesn’t allow access to the internet. The lack of Internet access provides an additional layer of security.
Route Table
Route Tables contain the rules (routes) determining how network traffic will be directed within your VPC and subnet.
Each subnet is linked to one Route Table.
What are the differences between Public & Private subnets?
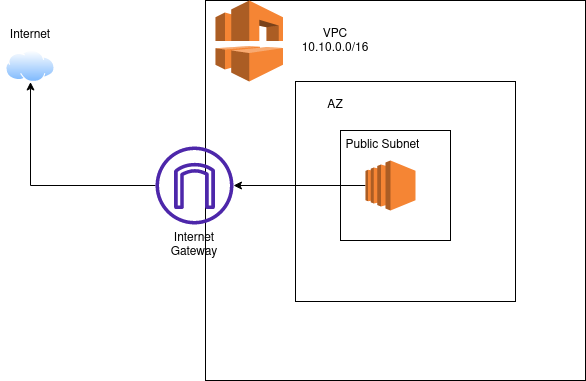
Public Subnet
A public subnet is a subnet that is associated with a Route Table that has a route to an Internet Gateway (Igw). This route allows access from the Public Internet to the subnet.
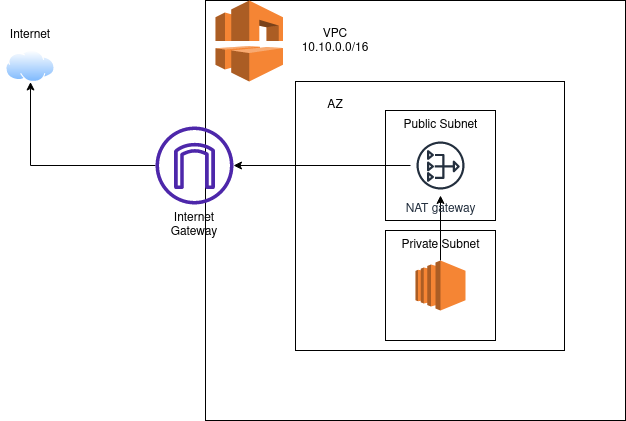
Private Subnet
A private subnet is a subnet that is associated with a route table that doesn’t have a route to an internet gateway. Resources in private subnets cannot communicate with the public internet.
AWS resources within the same VPC CIDR can communicate via their private IP addresses.
Resources in a private subnet can use the NAT Gateway to communicate to the Internet. A NAT Gateway is deployed in a public subnet.
When to use Public & Private Subnets?
Any AWS resource that doesn’t need access to the public internet should run in a Private subnet. Examples of such resources are your application servers or your database.
Resources like your Load Balancers that do require public internet access should be created in a public subnet.